Update: This pull request has been approved. Merged #102. The decoders for Penetration/Exploit/Hijacking tools are now merged to Dshell. Thanks to USArmyResearchLab and dev195!
Dshell is an extensible network forensic analysis framework and enables rapid development of plugins to support the dissection of network packet captures.
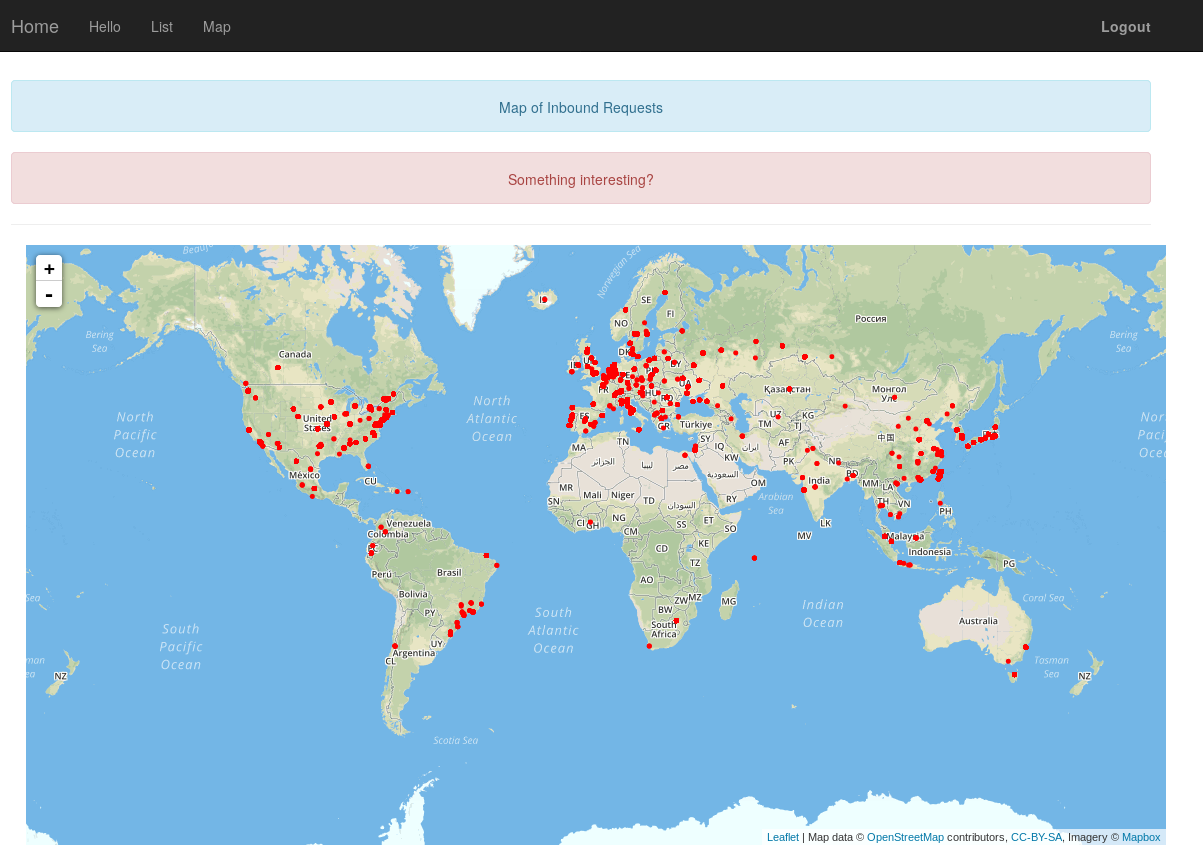
While I was updating my personal server I checked tons of malicious requests into the HTTP server. I decided to develop a simple “honeypot” for this kind of exploits attempts. With django I stored into a DB all HTTP headers and information about this attempts, also I printed in a world map all the connections made from June to September 2017, 29450 attempts in total!:
Honeypot Map
Penetration/Exploit/Hijacking Tools
Most of the Penetration/Exploit/Hijacking Tools use the HTTP methods to try to inject or execute code into the attacked server, also this tools usually have a well known “hardcoded” User-Agent, URI or request content. This attacks are looking to take advantage using a vulnerability in the system. This tools probes a port, network, api, or any other attack vector to find a vulnerability that can be exploited.
PHP exploits, Remote Code Execution, and SQL Injections are commonly used by this tools. Some of the most commons tools source and information:
Nmap: User-Agent header by default it is “Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)”. https://nmap.org/nsedoc/lib/http.html
Nessus: https://www.tenable.com/products/nessus-vulnerability-scanner
OpenVAS: http://www.openvas.org/src-doc/openvas-libraries/nasl__http_8c_source.html User-Agent header by default: #define OPENVAS_USER_AGENT “Mozilla/5.0 [en] (X11, U; OpenVAS)”
MASSCAN: https://github.com/robertdavidgraham/masscan
Morpheus: https://github.com/r00t-3xp10it/morpheus https://latesthackingnews.com/2016/12/19/morpheus-automated-ettercap-tcpip-hijacking-tool/
DataCha0s Web Scanner: http://eromang.zataz.com/2011/05/23/suc026-datacha0s-web-scannerrobot/ https://blogs.harvard.edu/zeroday/2006/06/12/data-cha0s-connect-back-backdoor/
HNAP (Home Network Administration Protocol): https://nmap.org/nsedoc/scripts/hnap-info.html
ZmEu Scanner: https://en.wikipedia.org/wiki/ZmEu_(vulnerability_scanner) http://linux.m2osw.com/zmeu-attack https://code.google.com/archive/p/caffsec-malware-analysis/wikis/ZmEu.wiki https://ensourced.wordpress.com/2011/02/25/zmeu-attacks-some-basic-forensic/ http://philriesch.com/computersecurity_zmeu.html
Jorgee Scanner: http://www.skepticism.us/2015/05/new-malware-user-agent-value-jorgee/ https://www.checkpoint.com/defense/advisories/public/2016/cpai-2016-0214.html https://blog.paranoidpenguin.net/2017/04/jorgee-goes-on-a-rampage/
Penetration/Exploit/Hijacking Tool decoder
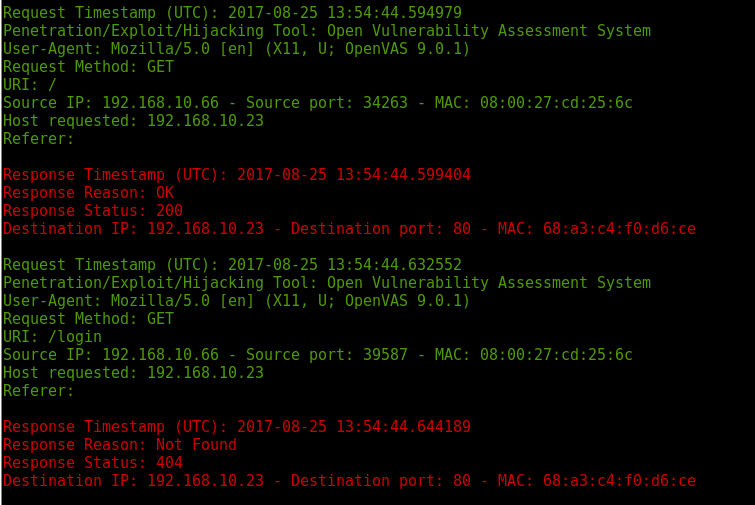
If the original scanner is not modified, can be detected. This is a PoC in order to generate simple rules to detect and identified some of the most commons Penetration/Exploit/Hijacking Tools. For example an OpenVAS scan:
Dshell> decode -d peht Openvas.pcap
Request Timestamp (UTC): 2017-08-25 13:54:44.594979
Penetration/Exploit/Hijacking Tool: Open Vulnerability Assessment System
User-Agent: Mozilla/5.0 [en] (X11, U; OpenVAS 9.0.1)
Request Method: GET
URI: /
Source IP: 192.168.10.66 - Source port: 34263 - MAC: 08:00:27:cd:25:6c
Host requested: 192.168.10.23
Referer:
Response Timestamp (UTC): 2017-08-25 13:54:44.599404
Response Reason: OK
Response Status: 200
Destination IP: 192.168.10.23 - Destination port: 80 - MAC: 68:a3:c4:f0:d6:ce
Request Timestamp (UTC): 2017-08-25 13:54:44.632552
Penetration/Exploit/Hijacking Tool: Open Vulnerability Assessment System
User-Agent: Mozilla/5.0 [en] (X11, U; OpenVAS 9.0.1)
Request Method: GET
URI: /login
Source IP: 192.168.10.66 - Source port: 39587 - MAC: 08:00:27:cd:25:6c
Host requested: 192.168.10.23
Referer:
Response Timestamp (UTC): 2017-08-25 13:54:44.644189
Response Reason: Not Found
Response Status: 404
Destination IP: 192.168.10.23 - Destination port: 80 - MAC: 68:a3:c4:f0:d6:ce
To obtain and show a detailed output we can use the --peht_showcontent option:
Dshell> decode -d peht --peht_showcontent <pcap>
Request Timestamp (UTC): 2017-07-16 02:41:47.238549
Penetration/Exploit/Hijacking Tool: Arbitrary Remote Code Execution/injection
User-Agent: Wget(linux)
Request Method: POST
URI: /command.php
Source IP: 1.2.3.4 - Source port: 666 - MAC: 67:b4:02:39:24:56
Host requested: example.com
cmd=%63%64%20%2F%76%61%72%2F%74%6D%70%20%26%26%20%65%63%68%6F%20%2D%6E%65%20%5C%5C%78%33%6B%65%72%20%3E%20%6B%65%72%2E%74%78%74%20%26%26%20%63%61%74%20%6B%65%72%2E%74%78%74
Response Timestamp (UTC): 2017-07-16 02:41:48.238549
Response Reason: Found
Response Status: 302
Destination IP: 192.168.1.1 - Destination port: 80 - MAC: a4:42:7b:56:b6:23
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>302 Found</title>
</head><body>
<h1>Found</h1>
<p>The document has moved <a href="https://example.com/command.php">here</a>.</p>
</body></html>