Update: This pull request has been approved. Merged #93. The decoders for SIP and RTP are now merged to Dshell. Thanks to USArmyResearchLab and dev195!
Dshell is an extensible network forensic analysis framework and enables rapid development of plugins to support the dissection of network packet captures.
While I was testing some VoIP packets, I discover that doesn’t exist VoIP specific decoders, so I created the first one to detect SIP Request and Response packets, and a second decoder to extract all the information for RTP packets used in a VoIP communication.
Screenshot
SIP decoder
SIP RFC 3261 indicate that SIP is a text-based protocol with syntax similar to that of HTTP. There are two different types of SIP messages:
- Requests initiate a SIP transaction between two SIP entities for establishing, controlling, and terminating sessions.
- Responses are send by the user agent server indicating the result of a received request.
A SIP session setup example can be similar to this one:
Alice's . . . . . . . . . . . . . . . . . . . . Bob's
softphone SIP Phone
| | | |
| INVITE F1 | | |
|--------------->| INVITE F2 | |
| 100 Trying F3 |--------------->| INVITE F4 |
|<---------------| 100 Trying F5 |--------------->|
| |<-------------- | 180 Ringing F6 |
| | 180 Ringing F7 |<---------------|
| 180 Ringing F8 |<---------------| 200 OK F9 |
|<---------------| 200 OK F10 |<---------------|
| 200 OK F11 |<---------------| |
|<---------------| | |
| ACK F12 |
|------------------------------------------------->|
| Media Session |
|<================================================>|
| BYE F13 |
|<-------------------------------------------------|
| 200 OK F14 |
|------------------------------------------------->|
| |
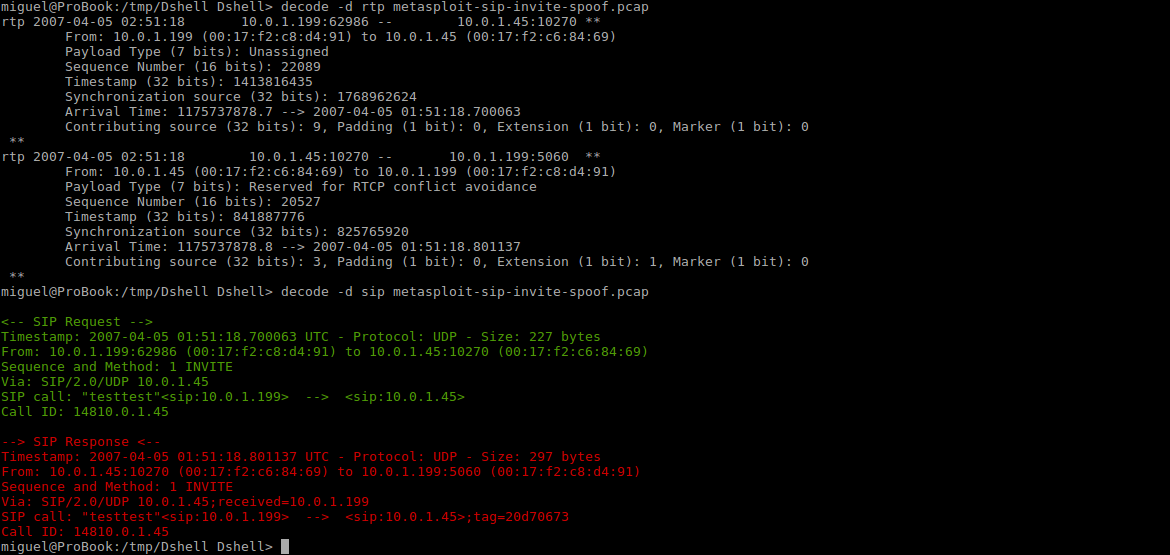
The Session Initiation Protocol (SIP) decoder will extract the Call ID, User agent, Codec, Method, SIP call, Host, and Client MAC address from every SIP request or response packet found in the given pcap. For example:
Dshell> decode -d sip <pcap>
<-- SIP Request -->
Timestamp: 2016-09-21 22:44:28.220185 UTC - Protocol: UDP - Size: 435 bytes
Sequence and Method: 1 ACK
From: 10.5.1.8:5060 (00:20:80:a1:13:db) to 10.5.1.7:5060 (15:2a:01:b4:0f:47)
Via: SIP/2.0/UDP 10.5.1.8:5060;branch=z9hG4bK940bdac4-8a13-1410-9e58-08002772a6e9;rport
SIP call: "M" <sip:M@10.5.1.8>;tag=0ba2d5c4-8a13-1910-9d56-08002772a6e9 --> "miguel" <sip:demo-alice@10.5.1.7>;tag=84538c9d-ba7e-e611-937f-68a3c4f0d6ce
Call ID: 0ba2d5c4-8a13-1910-9d57-08002772a6e9@M-PC
--> SIP Response <--
Timestamp: 2016-09-21 22:44:27.849761 UTC - Protocol: UDP - Size: 919 bytes
Sequence and Method: 1 INVITE
From: 10.5.1.7:5060 (02:0a:40:12:30:23) to 10.5.1.8:5060 (d5:02:03:94:31:1b)
Via: SIP/2.0/UDP 10.5.1.8:5060;branch=z9hG4bK26a8d5c4-8a13-1910-9d58-08002772a6e9;rport=5060;received=10.5.1.8
SIP call: "M" <sip:M@10.5.1.8>;tag=0ba2d5c4-8a13-1910-9d56-08002772a6e9 --> "miguel" <sip:demo-alice@10.5.1.7>;tag=84538c9d-ba7e-e611-937f-68a3c4f0d6ce
Call ID: 0ba2d5c4-8a13-1910-9d57-08002772a6e9@M-PC
Codec selected: PCMU
Rate selected: 8000
To obtain and show a detailed output we can use the --sip_showpkt option:
Dshell> decode -d sip --sip_showpkt <pcap>
--> SIP Response <--
Timestamp: 2016-09-21 22:44:25.360974 UTC - Protocol: UDP - Size: 349 bytes
From: 10.5.1.7:5060 (15:2a:01:b4:0f:47) to 10.5.1.8:5060 (00:20:80:a1:13:db)
SIP/2.0 100 Trying
content-length: 0
via: SIP/2.0/UDP 10.5.1.8:5060;branch=z9hG4bK26a8d5c4-8a13-1910-9d58-08002772a6e9;rport=5060;received=10.5.1.8
from: "M" <sip:M@10.5.1.8>;tag=0ba2d5c4-8a13-1910-9d56-08002772a6e9
to: <sip:demo-alice@10.5.1.7>
cseq: 1 INVITE
call-id: 0ba2d5c4-8a13-1910-9d57-08002772a6e9@M-PC
--> SIP Response <--
Timestamp: 2016-09-21 22:44:25.387780 UTC - Protocol: UDP - Size: 585 bytes
From: 10.5.1.7:5060 (15:2a:01:b4:0f:47) to 10.5.1.8:5060 (00:20:80:a1:13:db)
SIP/2.0 180 Ringing
content-length: 0
via: SIP/2.0/UDP 10.5.1.8:5060;branch=z9hG4bK26a8d5c4-8a13-1910-9d58-08002772a6e9;rport=5060;received=10.5.1.8
from: "M" <sip:M@10.5.1.8>;tag=0ba2d5c4-8a13-1910-9d56-08002772a6e9
require: 100rel
rseq: 694867676
user-agent: Ekiga/4.0.1
to: "miguel" <sip:demo-alice@10.5.1.7>;tag=84538c9d-ba7e-e611-937f-68a3c4f0d6ce
contact: "miguel" <sip:miguel@10.5.1.7>
cseq: 1 INVITE
allow: INVITE,ACK,OPTIONS,BYE,CANCEL,SUBSCRIBE,NOTIFY,REFER,MESSAGE,INFO,PING,PRACK
call-id: 0ba2d5c4-8a13-1910-9d57-08002772a6e9@M-PC
If your packets Ethernet is being replaced by Linux Cooked Capture we can use the next options:
Dshell> decode -d sip --no-vlan --layer2=sll.SLL <pcap>
And to obtain statistics about your SIP packets we can use tshark:
# tshark -q -r <pcap> -Y sip -z sip,stat
===================================================================
SIP Statistics
Number of SIP messages: 28
Number of resent SIP messages: 8
* SIP Status Codes in reply packets
SIP 180 Ringing : 1 Packets
SIP 200 OK : 5 Packets
SIP 100 Trying : 1 Packets
* List of SIP Request methods
INVITE : 4 Packets
PRACK : 1 Packets
INFO : 2 Packets
ACK : 1 Packets
PUBLISH : 10 Packets
CANCEL : 2 Packets
BYE : 1 Packets
* Average setup time 2447 ms
Min 2447 ms
Max 2447 ms
===================================================================
RTP decoder
RTP RFC 3550 provides end-to-end network transport functions suitable for applications transmitting real-time data, such as audio, video or simulation data, over multicast or unicast network services.
The RTP Payload is defined in the next RFCs and links:
The real-time transport protocol (RTP) decoder will extract the Hosts, Payload Type, Synchronization source, Sequence Number, Padding, Marker and Client MAC address from every RTP packet found in the given pcap. For example:
Dshell> decode -d rtp <pcap>
rtp 2002-07-26 07:19:10 10.1.6.18:2006 -- 10.1.3.143:5000 **
From: 10.1.6.18 (00:08:21:91:64:60) to 10.1.3.143 (00:04:76:22:20:17)
Payload Type (7 bits): PCMA - Audio - 8000 Hz - 1 Channel
Sequence Number (16 bits): 9825
Timestamp (32 bits): 54240
Synchronization source (32 bits): 4090175489
Arrival Time: 1027664350.17
Contributing source (32 bits): 0, Padding (1 bit): 0, Extension (1 bit): 0, Marker (1 bit): 0
**
rtp 2002-07-26 07:19:10 10.1.3.143:5000 -- 10.1.6.18:2006 **
From: 10.1.3.143 (00:04:76:22:20:17) to 10.1.6.18 (00:d0:50:10:01:66)
Payload Type (7 bits): PCMA - Audio - 8000 Hz - 1 Channel
Sequence Number (16 bits): 59364
Timestamp (32 bits): 55680
Synchronization source (32 bits): 3739283087
Arrival Time: 1027664350.2
Contributing source (32 bits): 0, Padding (1 bit): 0, Extension (1 bit): 0, Marker (1 bit): 0
**
Some data, to compare, obtained with tshark:
# tshark -q -r <pcap> -Y rtp -z rtp,streams
========================= RTP Streams ========================
Src IP addr Port Dest IP addr Port SSRC Payload Pkts Lost Max Delta(ms) Max Jitter(ms) Mean Jitter(ms) Problems?
10.1.3.143 5000 10.1.6.18 2006 0xDEE0EE8F ITU-T G.711 PCMA 236 0 (0.0%) 34.83 0.83 0.37
10.1.6.18 2006 10.1.3.143 5000 0xF3CB2001 ITU-T G.711 PCMA 229 1 (0.4%) 86.12 7.34 2.84 X